MS14-064 FREE DOWNLOAD
An intact copy can be downloaded here. The Veil Framework includes a few very good powershell payload delivery mechanisms. Version Product Milestone Service branch 6. Your feedback will help us improve the support experience. This module exploits a vulnerability found in Windows Object Linking and Embedding OLE allowing arbitrary code execution, publicly exploited in the wild as MS patch bypass. 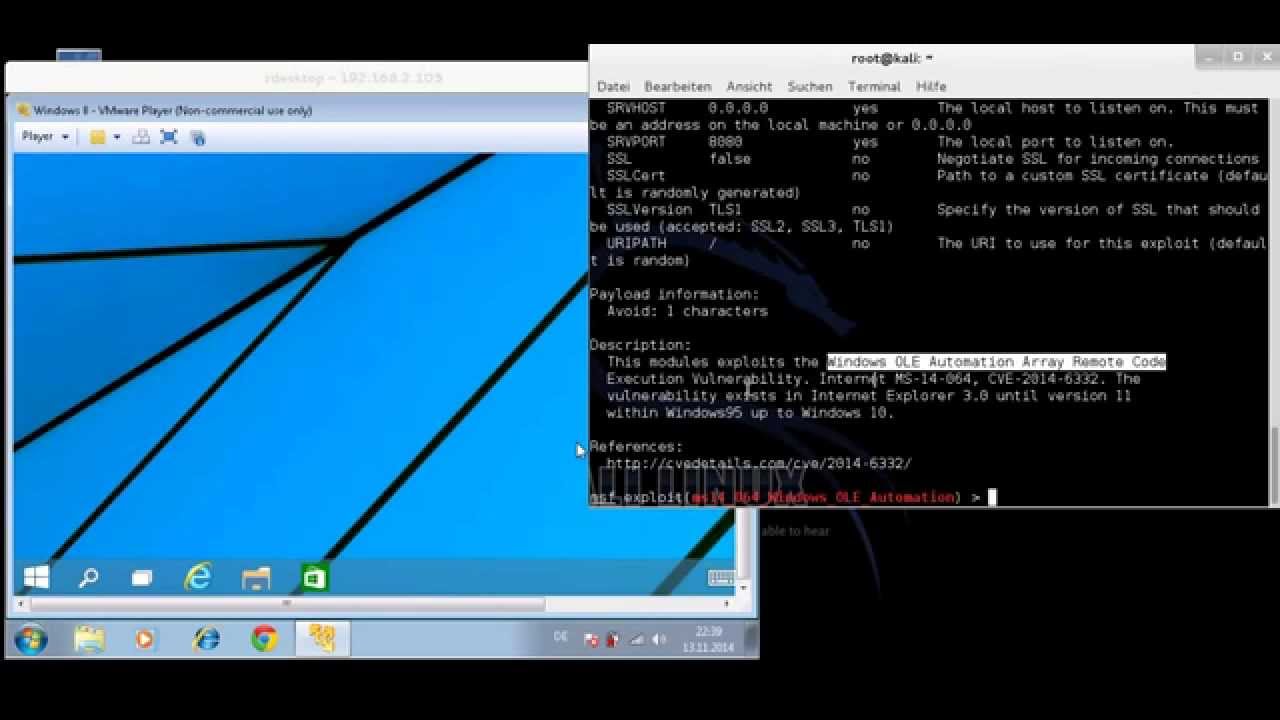
| Uploader: | Kigajin |
| Date Added: | 18 November 2004 |
| File Size: | 42.74 Mb |
| Operating Systems: | Windows NT/2000/XP/2003/2003/7/8/10 MacOS 10/X |
| Downloads: | 65516 |
| Price: | Free* [*Free Regsitration Required] |
Quick Cookie Notification This site uses cookies, including for analytics, personalization, and advertising purposes.
I'm sure some people must have tried to get this to work, if you did, you will know this this is an uphill battle with quotation marks. For more information, click the following article number to view the article in the Microsoft Knowledge Base: QFE service branches contain hotfixes in addition to widely released fixes. Your feedback will help us improve the support experience. Rapid7 Insight is your home for SecOps, equipping you with the visibility, analytics, and automation you need to unite your teams and amplify efficiency.
United States - English. Windows Vista and Windows Server file information The files that apply to a specific product, milestone SP nand service branch LDR, GDR can be identified by examining the file version numbers as shown in the following table: Did this solve your problem?
Please keep in mind that some other setups such as using Office SP1 might be less stable, and may end up with a crash due to a failure in the CPackage:: Crna Gora - Srpski.
New Zealand - English. Bosna i Hercegovina - Hrvatski.
MS Microsoft Windows OLE Package Manager Code Execution
We will be looking at the latter method. The dates and times for these files on your local computer are displayed in your local time and with your current daylight saving time DST bias. Ideally we want something which is as ms14--064 as possible and will be loaded straight into memory.
United Kingdom - English. The Microsoft update tried to fix the vulnerability publicly known as "Sandworm".

View Cookie Policy for full details. Microsoft has released security bulletin MS Veil Framework Ideally we want something which is as compact as possible and will be loaded straight into memory. Tell us what we can do to improve the article Submit. Description This module ms114-064 a vulnerability found in Windows Object Linking and Embedding OLE allowing arbitrary code execution, publicly exploited in the wild as MS patch bypass.
Indonesia Bahasa - Bahasa.
Patch Repository
All that remains is to fit the pieces above into the original POC. This site uses cookies, including for analytics, personalization, and advertising purposes. South Africa - English. The English United States version of this software update installs files that have the attributes that are listed in the following tables.
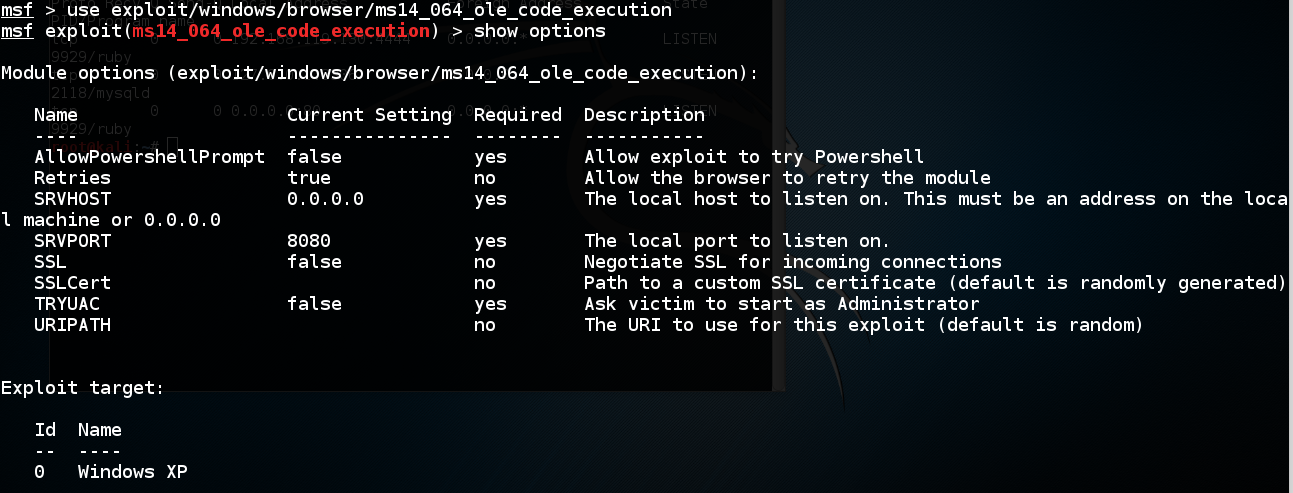
FuzzySecurity | Exploits: MS OLE Automation Array Remote Code Execution
Additionally we need to split up the base64 encoded string and the rest of the powershell wrapper. An intact copy can be downloaded here. Penetration testing software for offensive security teams. Products The Rapid7 Insight Cloud.
To display the available options, load the module within the Metasploit console and run the commands 'show options' or 'show advanced':. Additionally, the dates and times may change when you perform certain operations on the files. If you continue to browse this site without changing your cookie ms14-0064, you agree to this use.

Комментарии
Отправить комментарий